i4Q Solution IIoT Security Handler (i4QSH)¶
General Description¶
This document presents general description and technical application i4Q IIoT Security Handler (i4QSH) which is a proposal of an implementation of a Public Key Infrastructure (PKI) to provide trust in the i4Q Industrial Control System (ICS) ecosystem.
An ICS is a collection of control systems that work together to achieve a certain industrial goal. The integration of operational technology (OT) and information technology (IT) in ICS has boosted operational and financial efficiency, but it has also opened the door to greater risks, including system outages and espionage. Today a control system is vulnerable to cyber-attacks in many ways and control system engineers need to be well aware of subjects such as ICS security and SCADA security. This document presents a proposal to use X.509 certificates to provide trust in i4Q ICS ecosystem. This document presents a proposal to use X.509 certificates to provide trust in i4Q ICS ecosystem.
PKI is used to create a trust chain that allows a person, service, machine, or application to be authorized, a secure connection to be formed, or the provenance of software or documents to be validated. This is accomplished through certificates, which a PKI creates, manages, and distributes while also having the ability to revoke. The public key in a certificate must be kept safe and secret, and the private key must be kept safe and hidden as well. It’ll have to be stored in a hardware security module (HSM).
Features¶
The main aspects considered in i4QSH are as follows:
Authentication: The PKI allows trading partners to be identified online through trustworthy authorities that are in charge of issuing digital certificates and providing procedures for identifying individuals who hold those certificates on behalf of a company.
Privacy: The technique for protecting information is provided by digital certificates. Messages can be encrypted to reduce the danger of them being intercepted or read by someone other than the intended receiver while in transit.
Integrity: When conducting business over the Internet, a company needs to know that any transaction conducted or information provided will not be altered or interfered with during transmission. As a fundamental component, the PKI ensures transaction security. The recipient of a communication can use PKI to verify that the message is still the same as it was when it was transmitted.
Non-repudiation: As a fundamental component, the PKI ensures transaction security. The recipient of a communication can use PKI to verify that the message is still the same as it was when it was transmitted.
ScreenShots¶
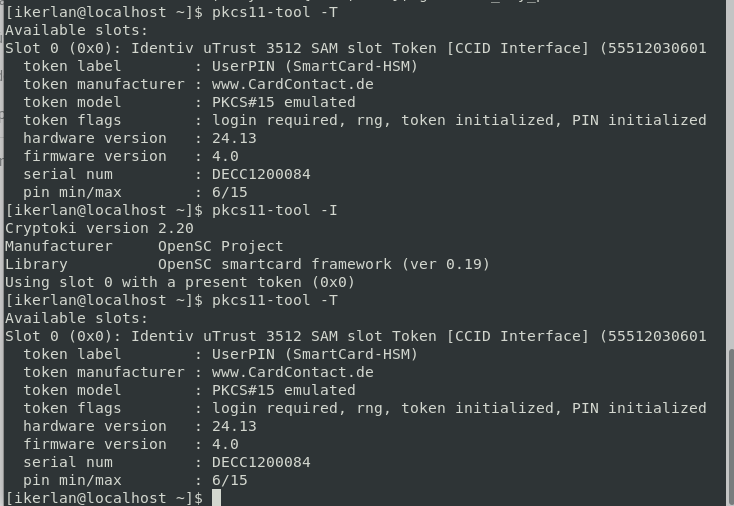
Getting HSM information from console¶
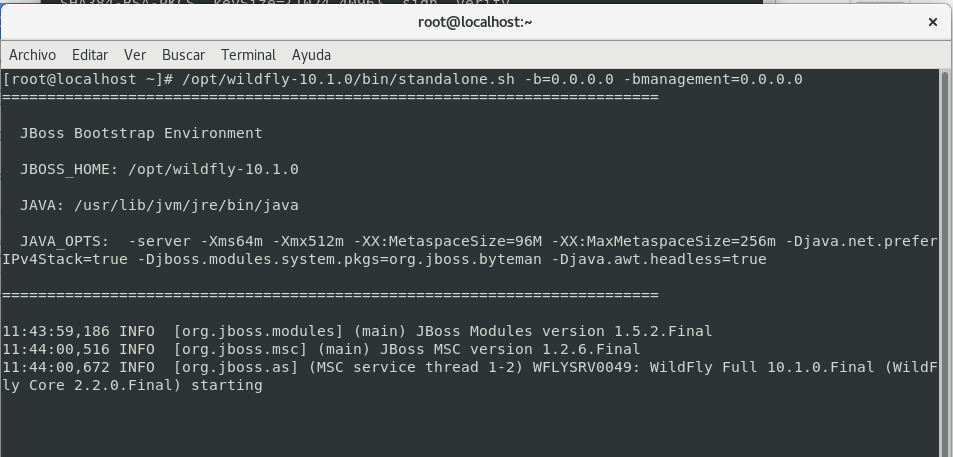
Bootstrapping Ejbca PKI instace from console¶
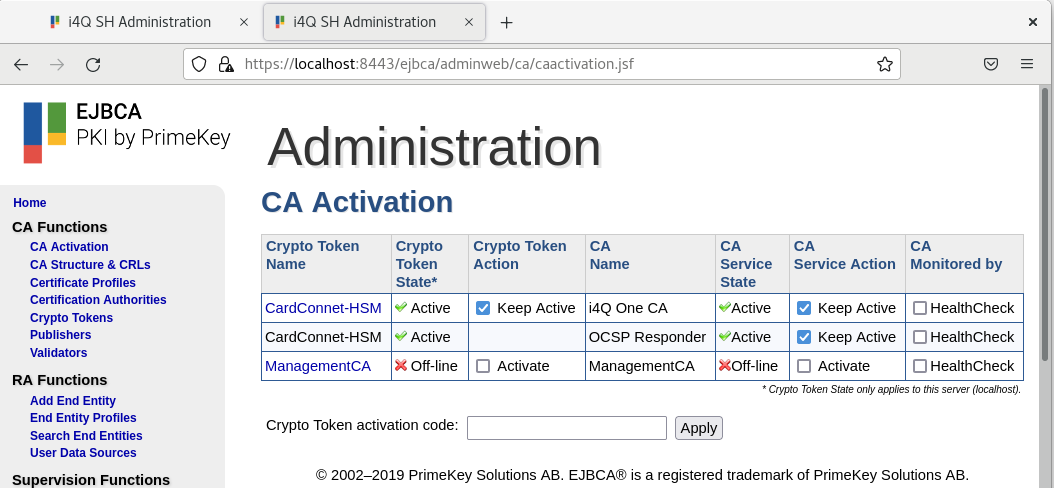
View of Ejbca and HSM configured to use¶
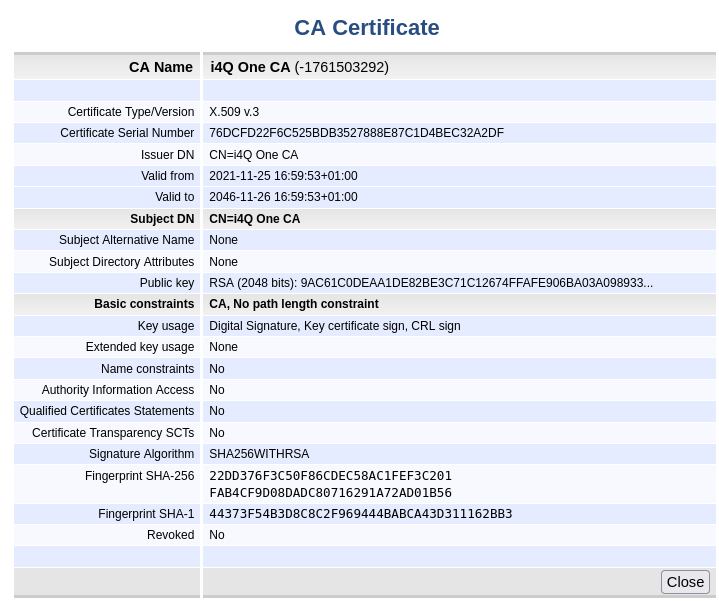
View of an i4Q CA certificate¶
Comercial Information¶
Technical development¶
Library: openSSL
License¶
Dual license AGPLv3 or PRIVATE
Pricing¶
Subject |
Value |
|---|---|
Payment Model |
Quotation under request |
Price |
Quotation under request |
Associated i4Q Solutions¶
Required¶
Currently, it can operate without the need for another i4Q solution.
Optional¶
None. However, the i4QSH is expected to be used with almost any other i4Q solution in the pilots, where security is need providing SSL certificates to trust data and communications, for example in the i4QDR solution.
System Requirements¶
Windows or Linux powered PC
VMware or VirtualBox CentOS image
CardContact HSM.
- CentOS requirements:
4 GB Ram
2 CPU
64-bit operating system
Hardware virtualisation support
Additionally, it requires the following dependencies to be already installed:
- OpenSC, required security library to interact with HSM.
:> wget http://mirror.centos.org/centos/7/os/x86_64/Packages/opensc-0.19.0-3.el7.x86_64.rpm
- EJBCA, PKI software administrator.
:> wget https://sourceforge.net/projects/ejbca/files/ejbca6/ejbca_6_15_2_6/ejbca_ce_6_15_2_6.zip
API Specification¶
Since i4QSH is expected to be used or integrated with other i4Q solutions, the plan is to use Web Service API as a mechanism to interact with the i4QSH. This WS API offers the following endpoints:
https://HOST-IP:8443/ejbca/ejbcaws/ejbcaws?wsdl
Providing links to access to the required functions to interact with PKI.
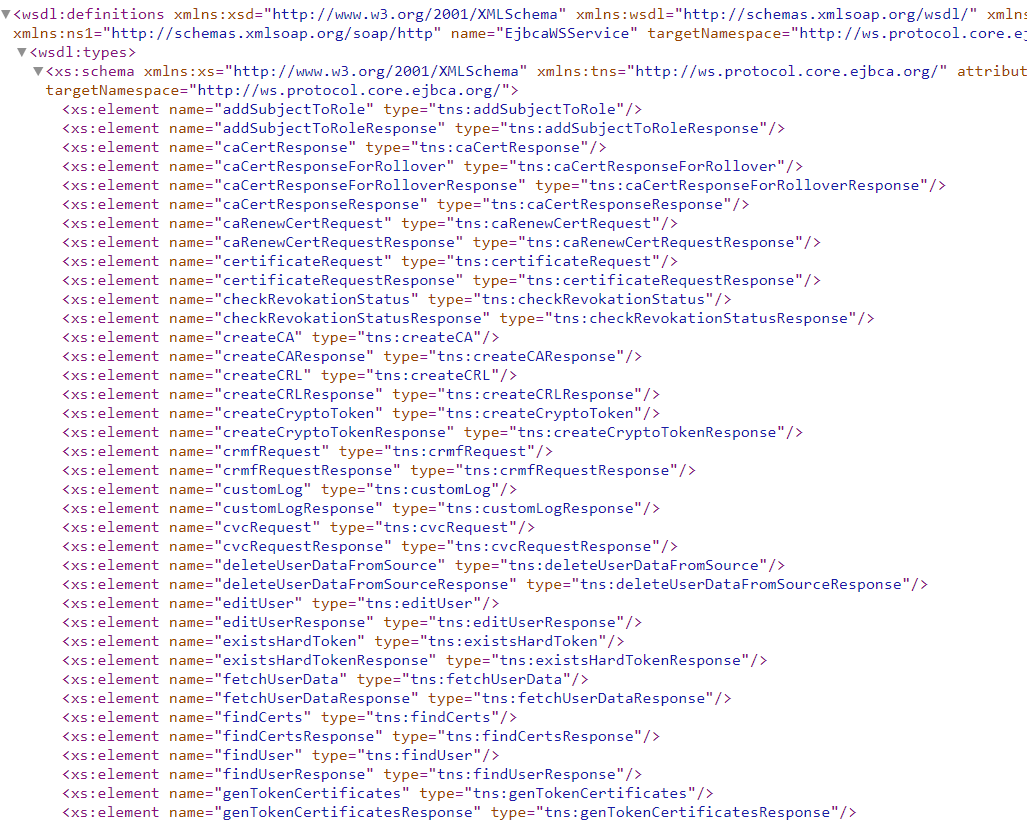
WS-API functions provided by PKI¶
Installation Guidelines¶
Resource |
Location |
|---|---|
Last release (v.1.0.0) |
Installation CardContact HSM¶
- Latest installation information at:
Command to initial installation of HSM: sc-hsm-tool:
[root@localhost ~]# sc-hsm-tool –initialize –so-pin xxxxxx –pin yyyyyy
Installation EJBCA¶
- Latest installation information at:
Need to adapt web.properties file in ejbca/conf to use CardContact HSM:
cryptotoken.p11.lib.60.name=OpenSC
cryptotoken.p11.lib.60.file=/usr/lib64/opensc-pkcs11.so
Installation Open62541¶
Latest installation information at: https://www.open62541.org/
- Commands to install Open62541:
[root@localhost ~]# cmake .. -DCMAKE_INSTALL_PREFIX=/home/maialen/install -DUA_ENABLE_SUBSCRIPTIONS=ON -DUA_ENABLE_ENCRYPTION=ON -DCMAKE_BUILD_TYPE=RelWithDebInfo -DUA_NAMESPACE_ZERO=Full .. [root@localhost ~]# make
User Manual¶
How to use EJBCA¶
The resulting solution is based on the external program Ejbca to configure and manage the PKI infrastructure. Latest guidelines in how to operate will be find at https://download.primekey.com/docs
WS-API¶
The SOAP API is compatible with all development languages that can handle SOAP messages. This includes programming languages such as Java, C# and PHP. Client stubs are generated from the WSDL file, which includes all information to use the WS API. The WSDL can be accessed from your installed EJBCA at https://HOST-IP:8443/ejbca/ejbcaws/ejbcaws?wsdl.
How to use Open62541¶
- Compile and execute the code server and client:
[root@localhost ~]# gcc -std=c99 -I$HOME/install/include -L$HOME/install/lib server.c -lopen62541 -lmbedtls -lmbedx509 -lmbedcrypto -o server [root@localhost ~]# gcc -std=c99 -I /home/user/install/include -L /home/user/install/lib server.c -lopen62541 -lmbedtls -lmbedx509 -lmbedcrypto -o client [root@localhost ~]# .server [root@localhost ~]# .client
